Facebook hack
On Sunday 10th April 2022 my Facebook account of 16 years was hacked and subsequently disabled by Facebook for “violating Community Standards” – in other words posting extreme content that earned an immediate ban.
My account was secured with two-factor authentication and a strong 20 character random password. According to one source, it would take a computer over 34,000 years to crack such a password.
There are a number of possible vulnerabilities that allowed this to happen. I will lay out the timeline and vulnerabilities here but the only conclusion I can come to is that either Facebook systems were insecure, compromised or the hack came from within the Facebook organisation itself. This is not as far fetched as it sounds. In 2018, the respected tech blog techcrunch.com reported the following:
For one thing, the network has grown so large that its surface area is impossible to secure completely. That was certainly demonstrated Friday when it turned out that a feature rollout had let hackers essentially log in as millions of users and do who knows what. For more than a year.
I lay out the timeline below that brings me to that conclusion
Timeline
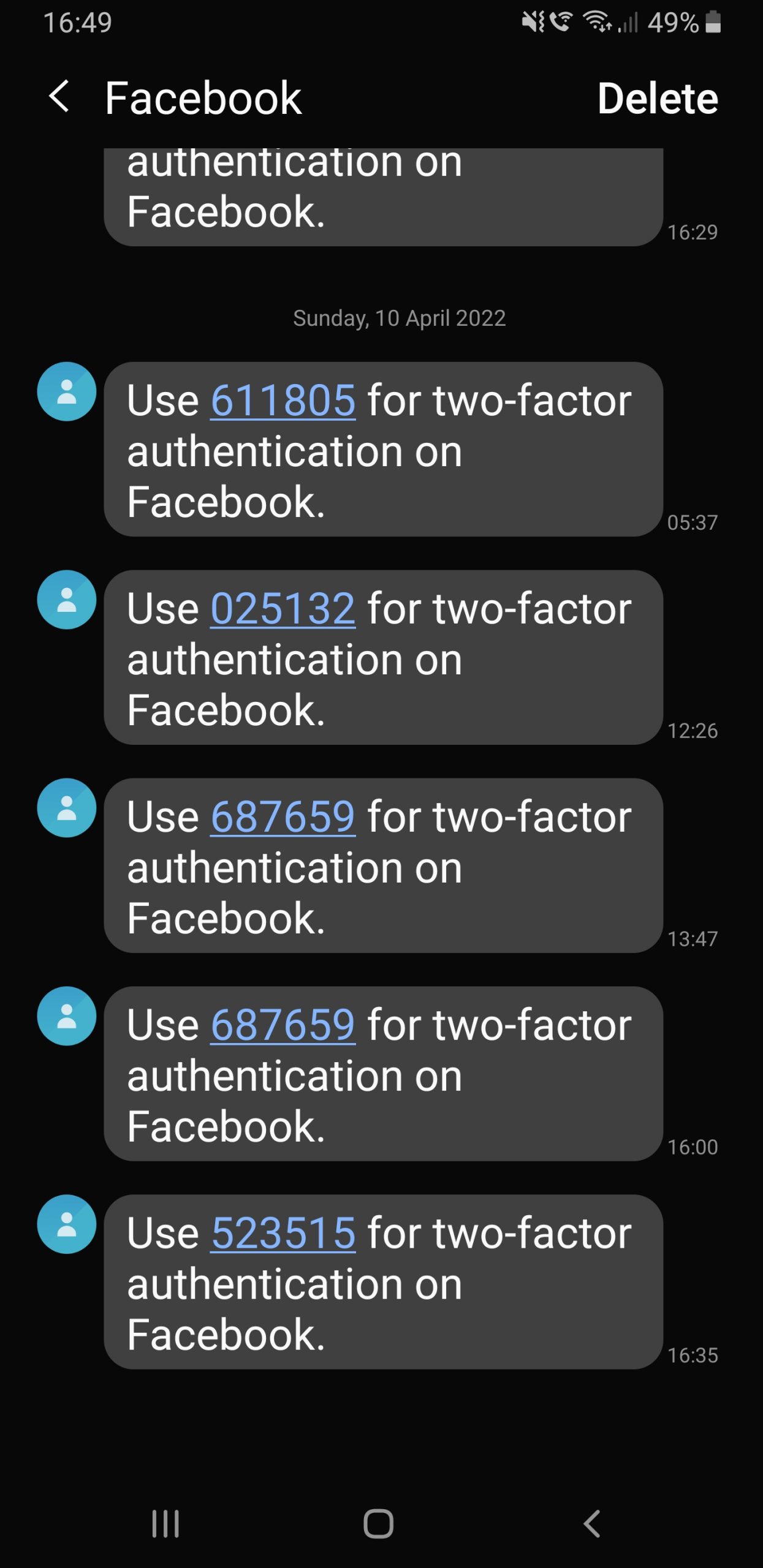
05:37
Unsolicited 2FA code received
The first code arrived at 5:37 am. This alerted me to my password being compromised. As it was 5:37 in the morning and I had 2FA in place I ignored it.
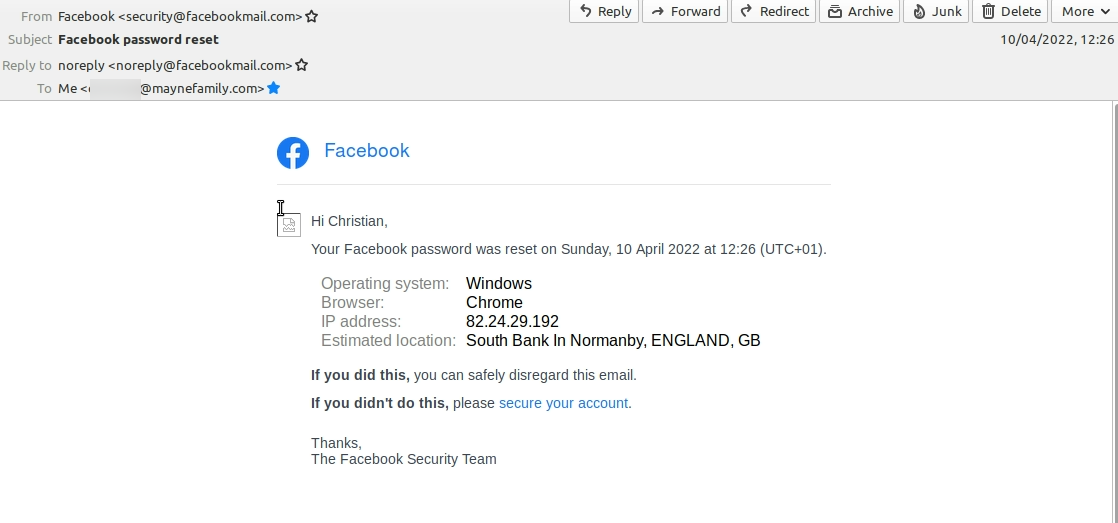
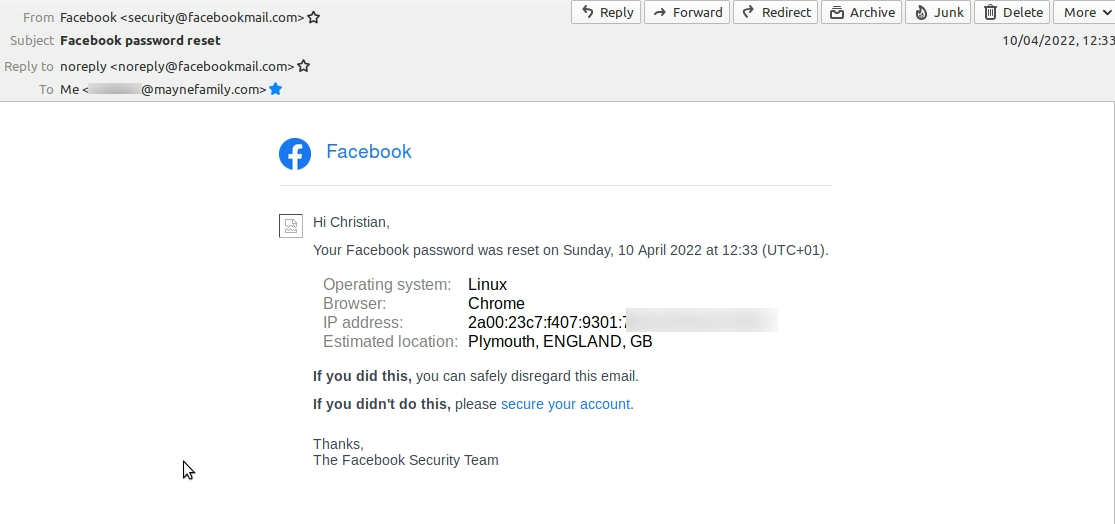
12:26
Second Unsolicited 2FA code received and password reset
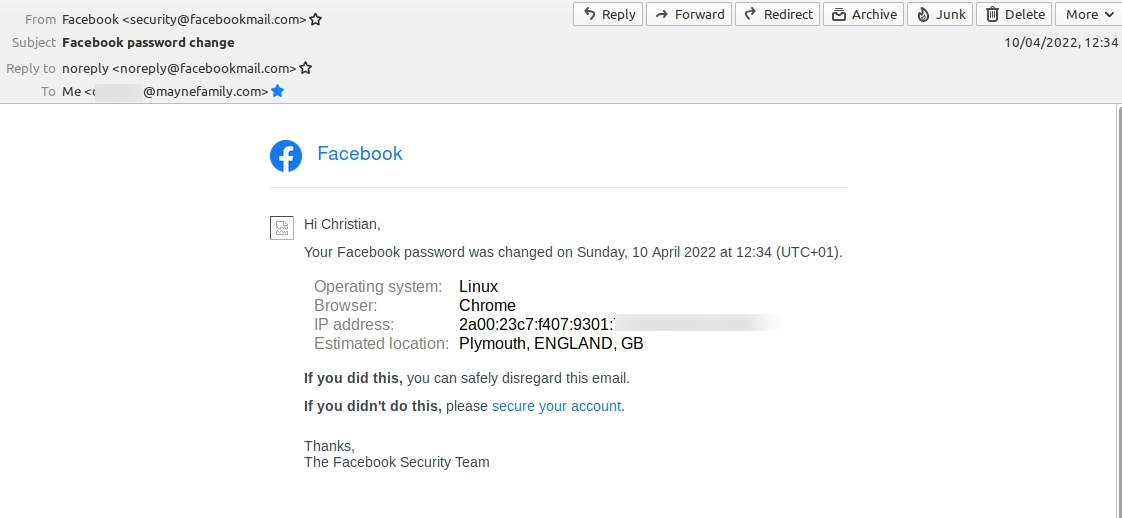
Second 2FA code arrives.
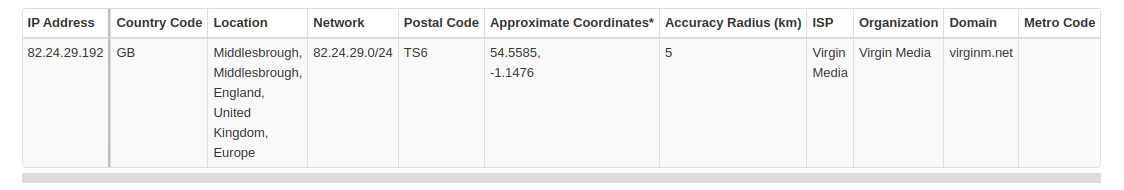
Moments later I receive an email telling me my password has been reset on a Windows PC using the IP address 82.24.29.192 in Normanby, England. I don’t have a Windows PC – I exclusively use Linux Mint – and I am based in Plymouth, Devon.
The IP address 82.24.29.192 is operated by Virgin Media
At this point it’s clear my 2FA has been breached somehow. There are a number of possible vectors for this, none of which seem to have been used – more about that later.
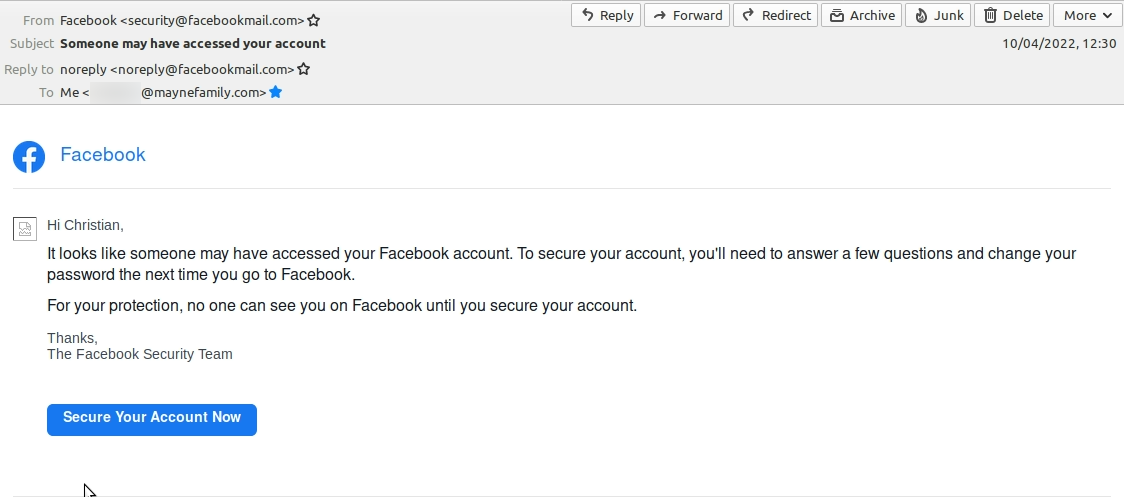
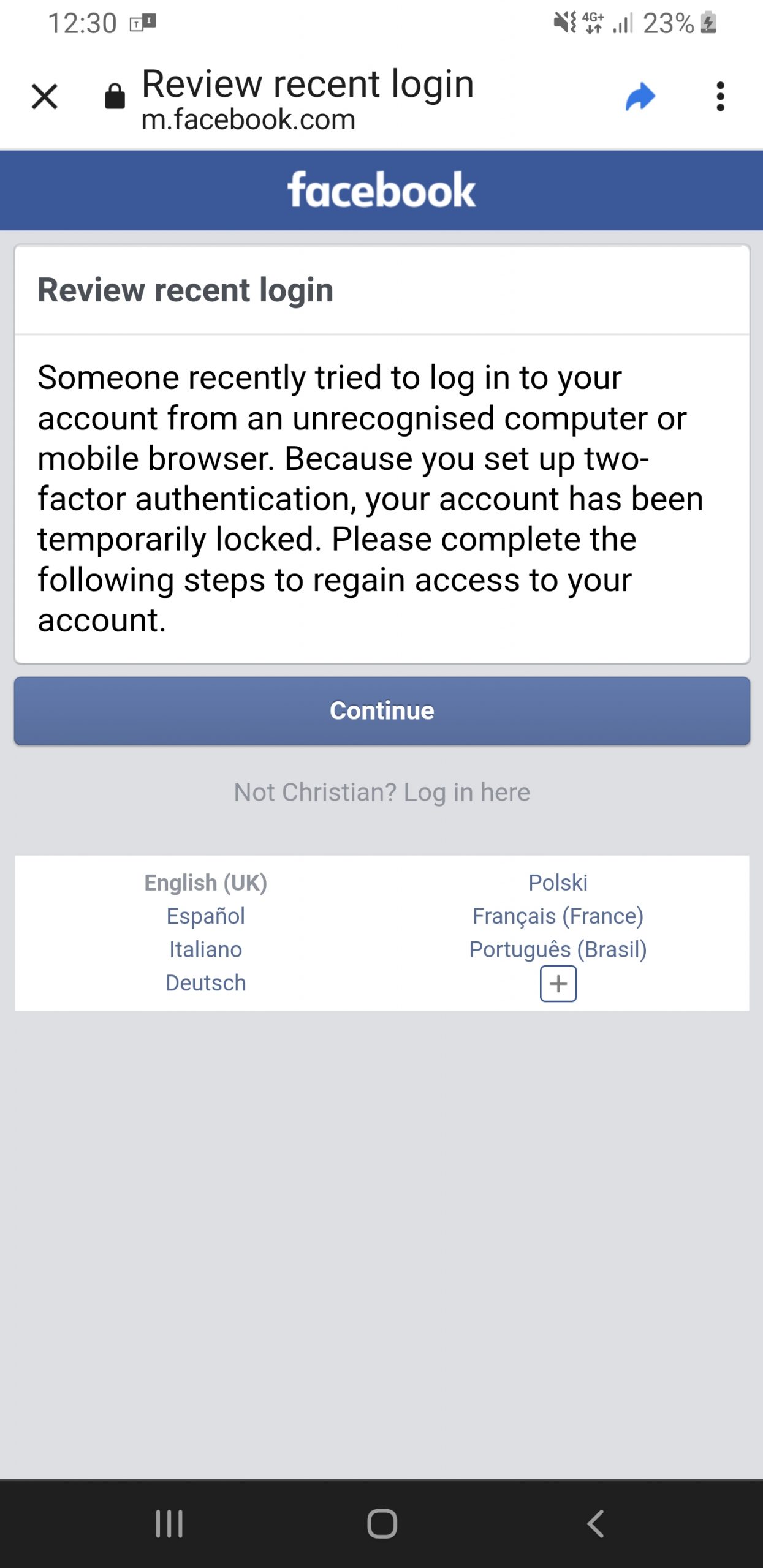
12:30
Report breach to Facebook
I confirm that the Facebook password change was not initiated by me. Facebook send me an email inviting me to secure my account.
I log into my account and am advised that 2FA has prevented the user from logging in and the account has been locked.
The screenshot taken below is timestamped 12:30:38
12:31
Facebook forces a password change
I am forced top change my password and use the Keeper Security password manager to generate a 20 character unique randomised password
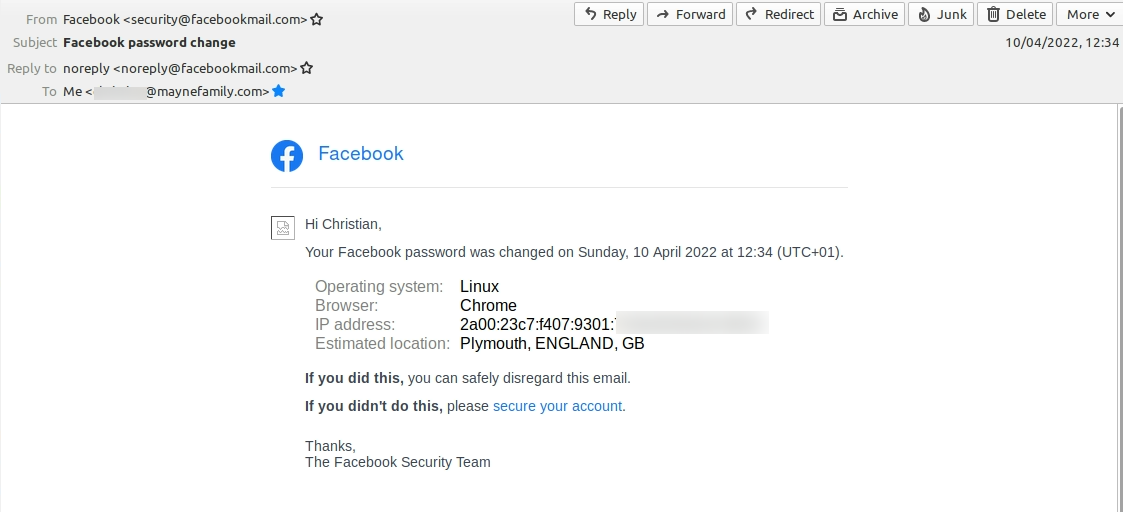
12:33 – 12:34
Facebook forces me to change password twice in quick sucession
I am forced top change my password two times in quick sucession whcich I once again do using the Keeper Security password manager to generate a 20 character unique randomised password
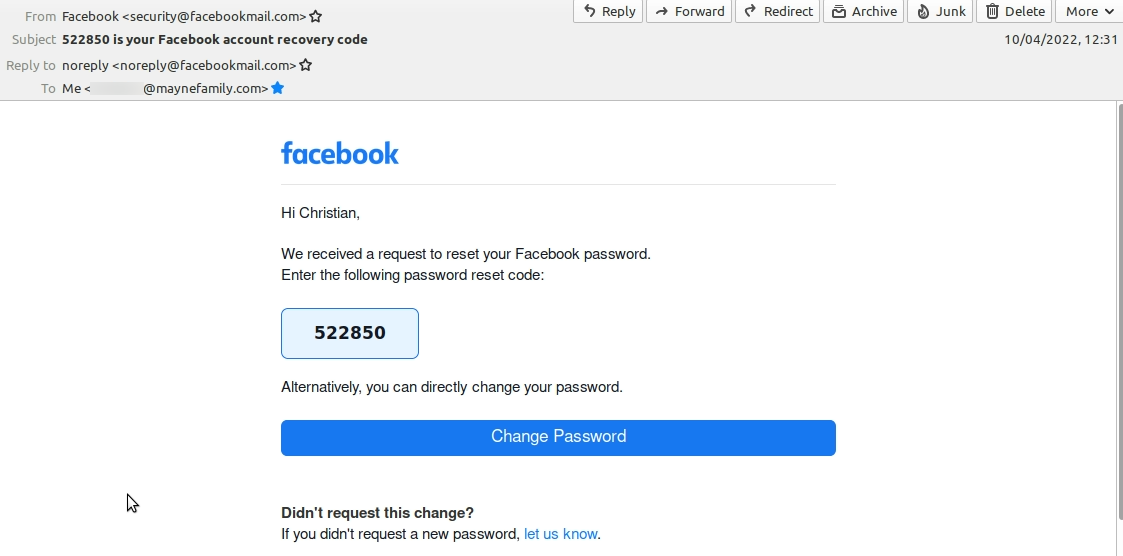
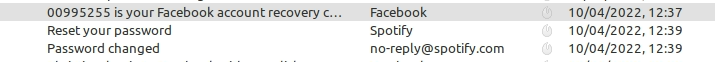
12:37
Facebook sends me an unsolicited account recovery code
Another account recovery code arrives at 12:37 but I miss this as I am getting ready to leave the house
12:39
Spotify password changed
Bizarrely, my Spotify password is changed. I only have a free spotify account which I haven’t used in ten years or so. I don’t notice this until later
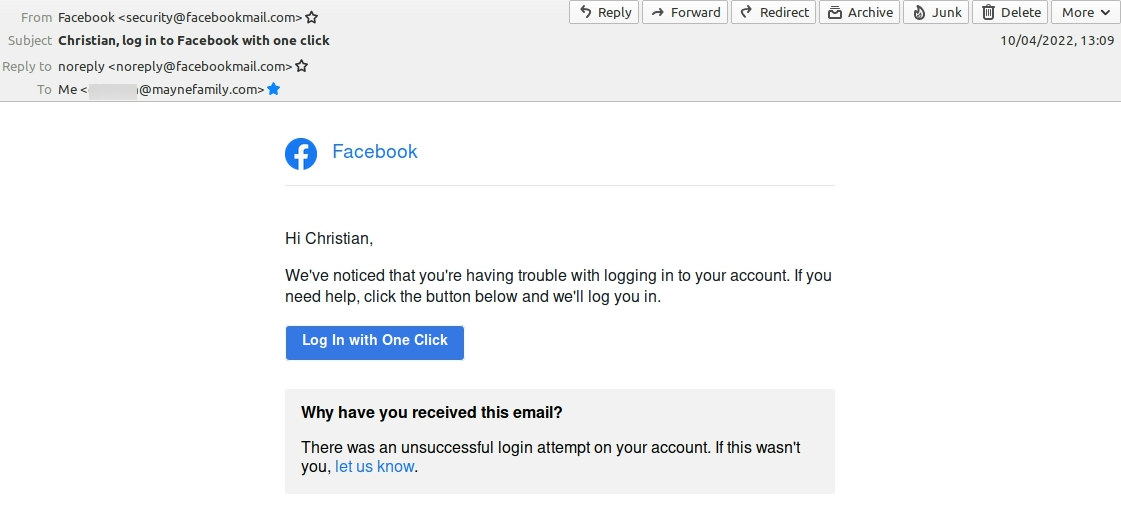
13:09
Facebook send me an unsolicted “one click” Login
We’ve noticed that you’re having trouble with logging in to your account. If you need help, click the button below and we’ll log you in.
What the actual Fuck?!
I have already reported my account as being compromised but they decide to send me an email with a direct login link, bypassing 2FA, out of the blue.
As if the correct response to a brute force attempt is to send a link bypassing security.
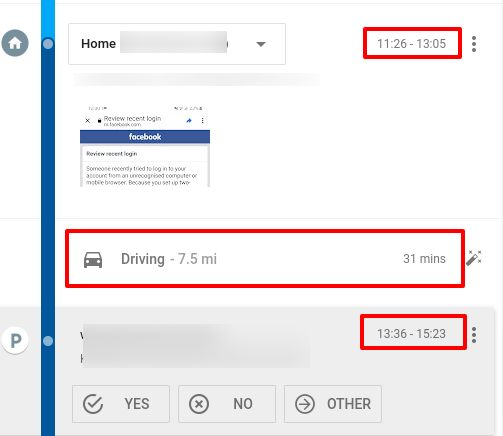
Worth noting I am already out of the house and driving at this point – my Google Maps timeline below.
Now I think the reason for the hack is clear is becoming clear. My email password had been compromised allowing a user to see recovery codes and bizarrely Facebook decided it would be a good idea to entirely bypass 2FA and send a “one click” login code to the email address.
This is precisely what multi-factor authentication is designed to protect against
I suggest this is a huge security flaw in Facebook that borders on negligence.
13:46
Facebook sends me another unsolicited account recovery code
Another account recovery code arrives at 13:46 but I miss this as I am already out of the house. Assuming my email had been compromised, a hacker would be able to access this code.
13:47
Facebook sends another 2FA Code
I am already out of the house at this point and miss this. Curiously the code sent is identical to the code sent at 16:00 when I attempted to login. See image above.
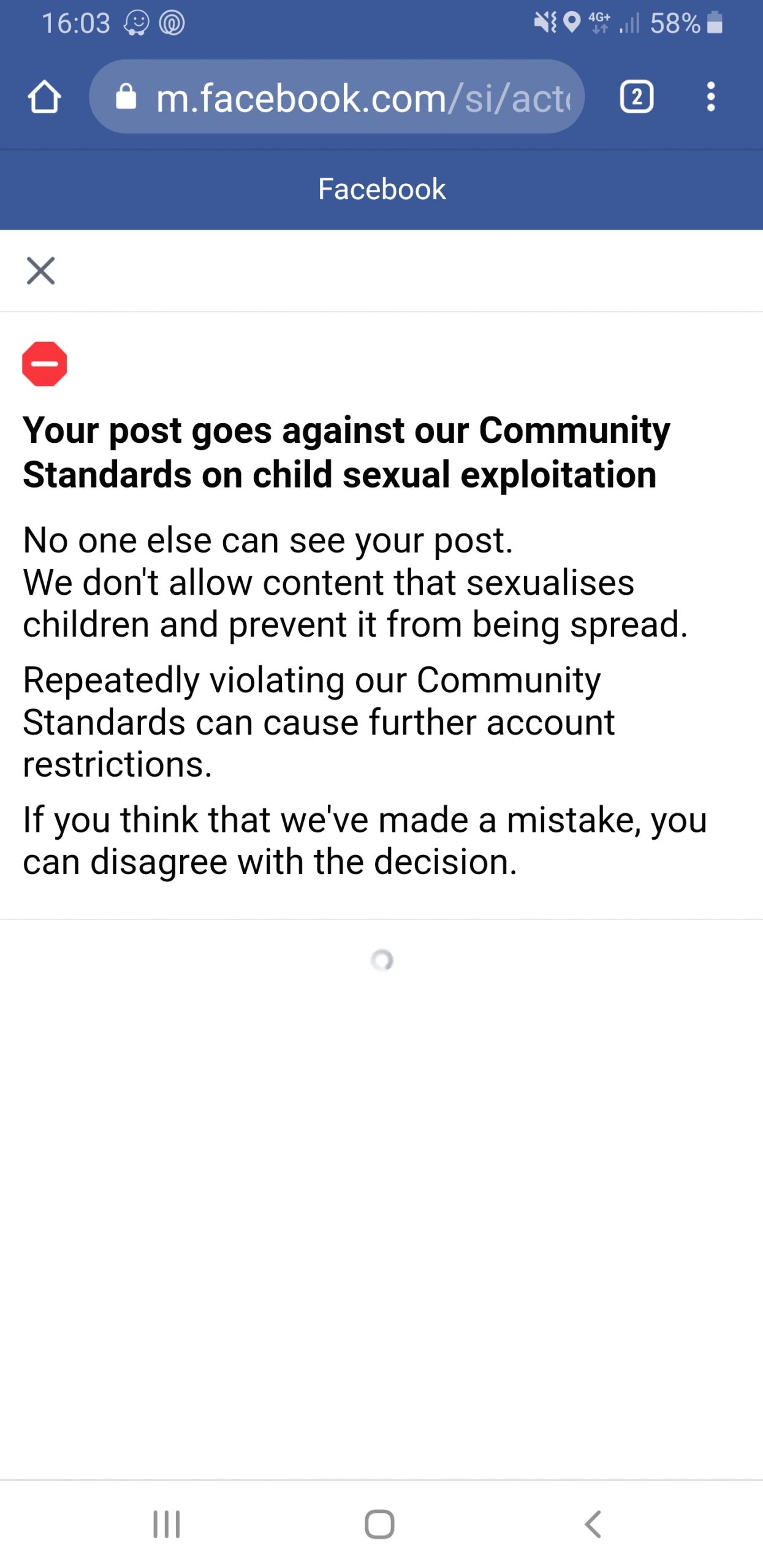
16:03
Account suspend due to “violating community standards”
After securing my account at 12:34, the next I am aware of any problems was when I tried to login to Facebook Messenger to finalise an appointment arrangement. I receive a 2FA code as usual which is accepted and I login in (see image above. Interesting to note the same code as was sent at 13:47 when the account was compromised is sent again at 16:00 when I attempted to login – coincidence or glitch?
At this point I am immediately locked out of my account for posting content that goes against the community standards on child sexual exploitation.
This was pretty shocking, but it is a standard tactic used by hackers to permently disable accounts so that associated assets (groups, pages, ad accounts) can be more easily taken over.
This has been reported in multiple news outlets such as this Australian article from October 2021: Hackers using child exploitation images to disable people’s Facebook accounts
16:04
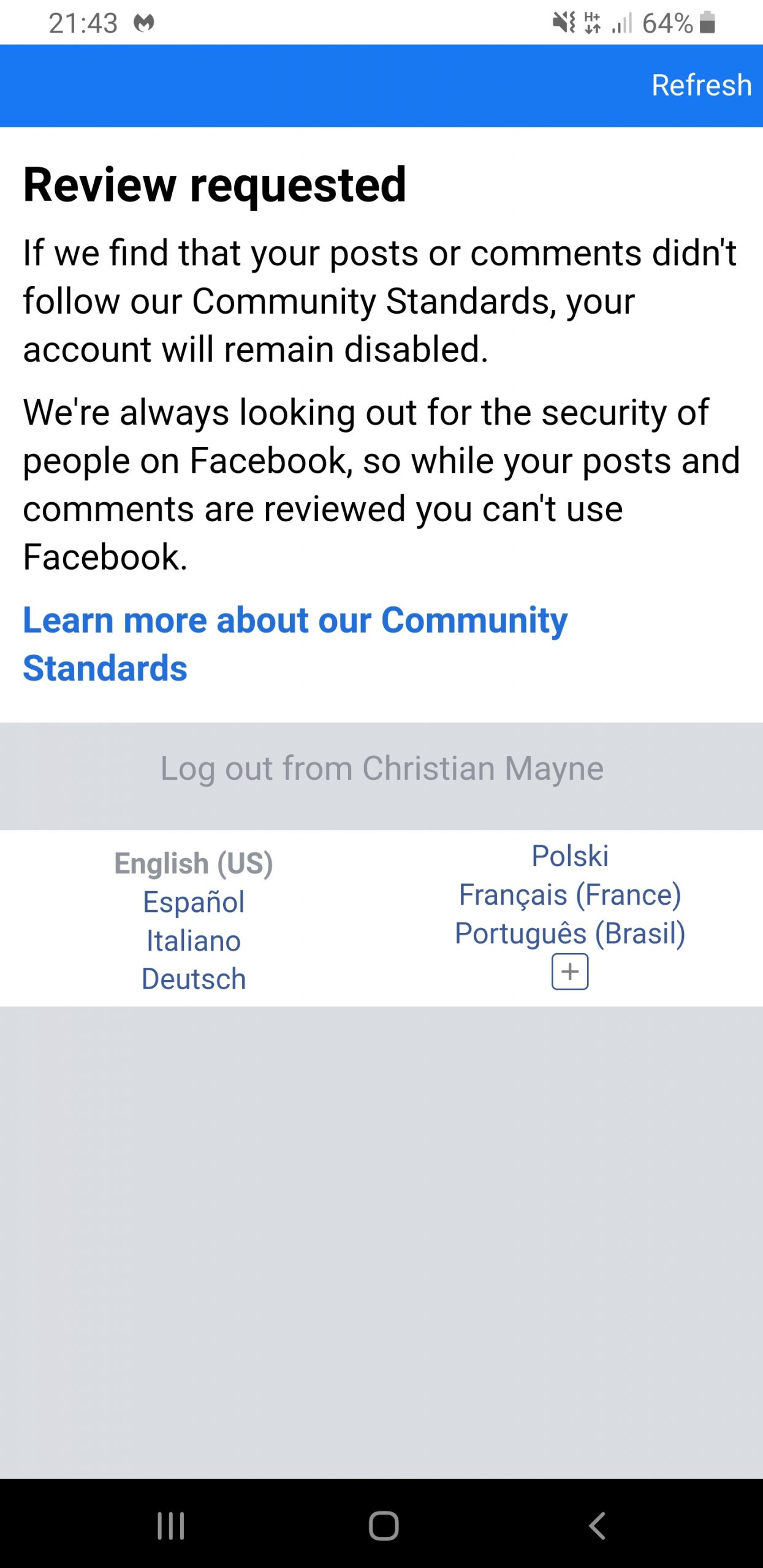
I appeal the decision
I appeal the decision, but note the appeal is about the content of the post, not the hacked account, so my suspicion is the appeal will be denied.
My account is currently counting down from 30 days at which point my account will be “permently deleted”, along with my wedding photos, photos of my children, access to my business pages (that I spend hundreds of pounds monthly promoting with Facebook Ads!), business contacts gleaned through these pages, access to the groups I administer (I am the administrator on two groups with 20000+ members), contact with my family overseas, etc.
I’m not taking the decision lying down.
11th April
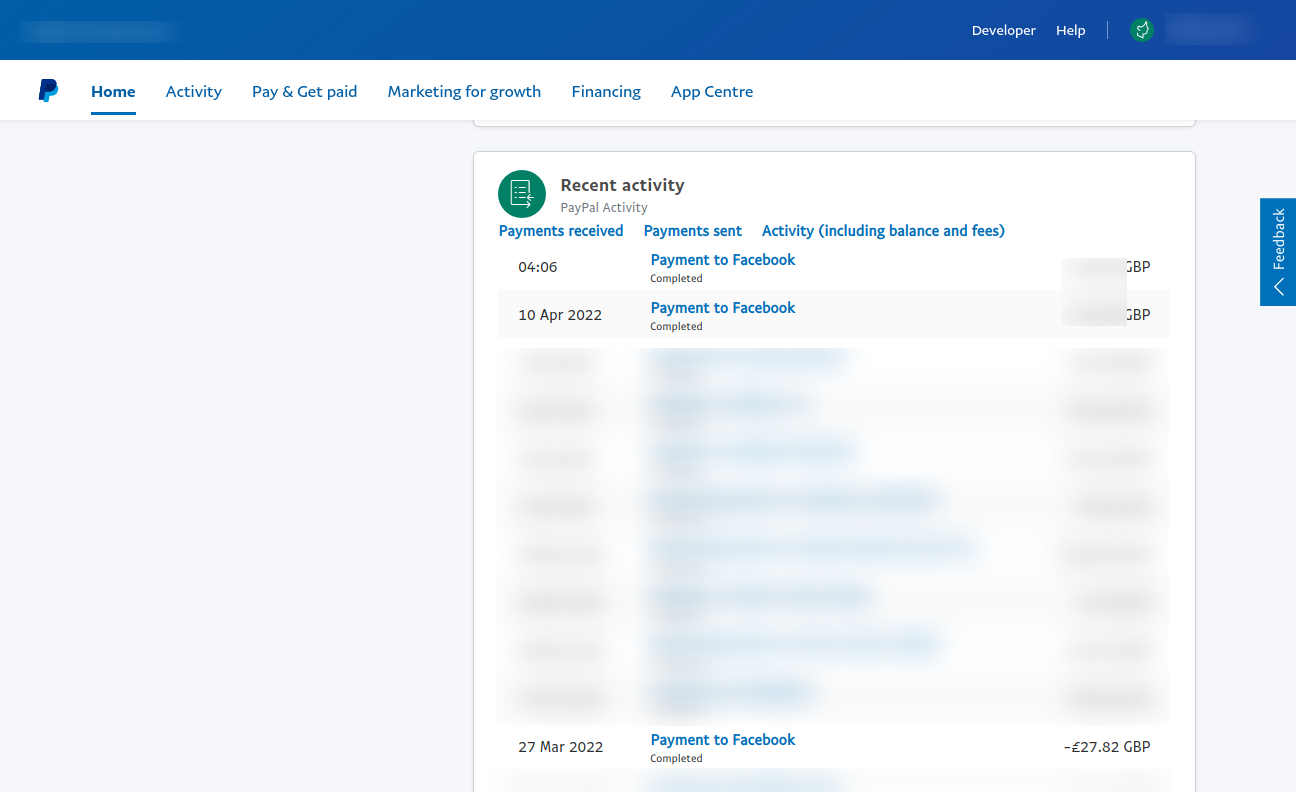
Facebook Ads account compromised and budget changed
I then received two charges against my Paypal account in quick sucession (around 8 hours) for Facebook Ads at 20x my daily ad budget.
Paypal have now reveresed these charges, but Facebook – on one of the few pages I can access through an emergency backup account I have against FBs Terms & Conditions – are marking my account as in arrears due to these charge reversals.
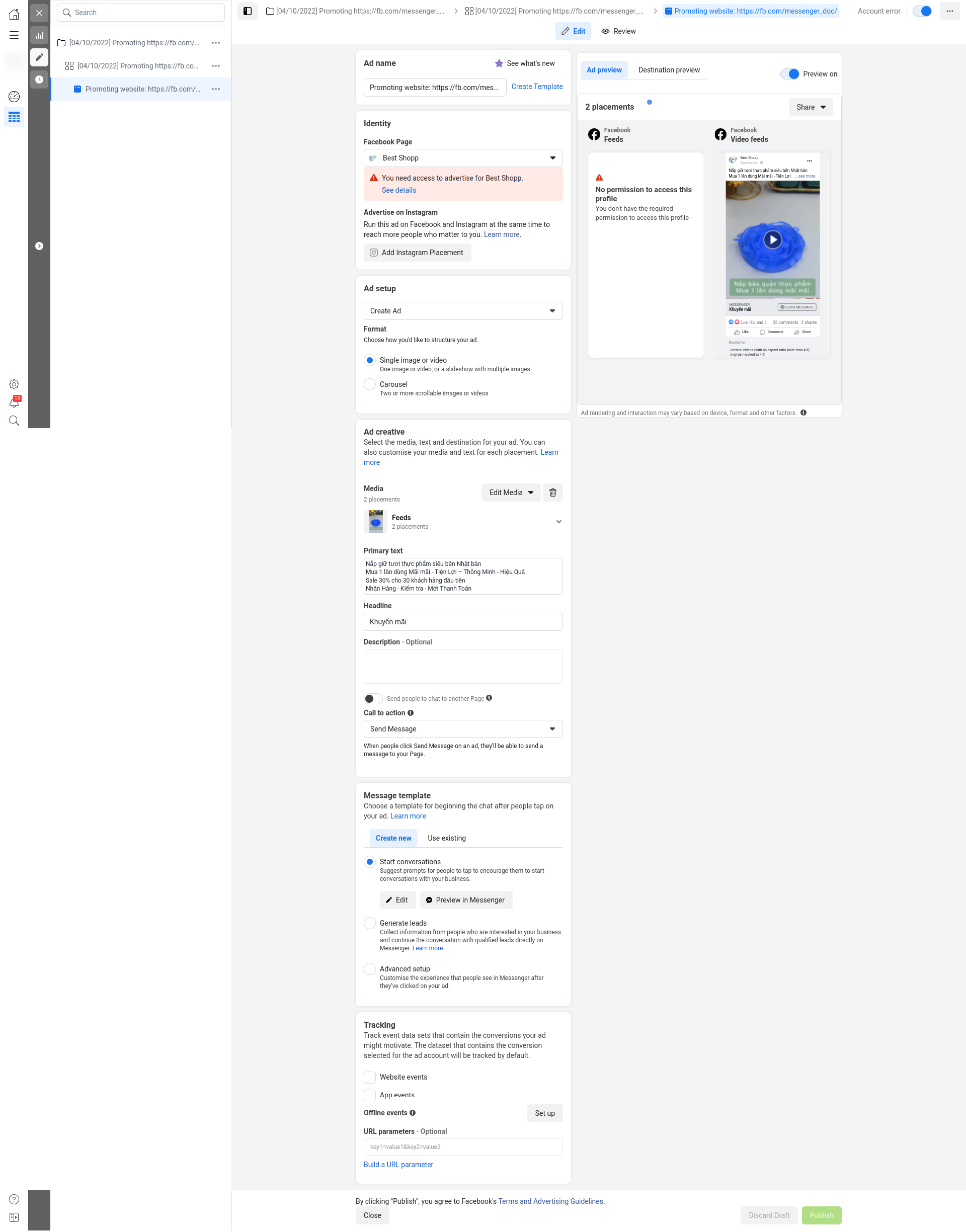
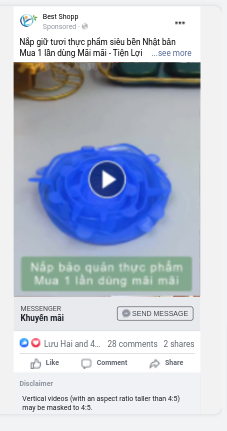
The ads appear to be for “Best Shopp”. The ads are still active within the ad account and are only not running -despite being clearly fraudulent – because I have cancelled my Paypal agreement.
We are now 4 days into this debarcle. My account and business assets are all disabled – and very probably lost forever – the fraudulent ads are still active on my Facebook Ads account and my the Facebook Page “Best Shopp” is still active though I can’t see it, probably due to geo targeting.
I have spent nearly four days almost fuill time trying to find someone at Facebook who will investigate the issue. I have been documenting some of these communications here: http://christian.maynefamily.com/category/facebook/